Adding FiveM to Your network Filter: A Comprehensive Guide
FiveM, a popular modification for Grand Theft Auto V, allows players to experience customized role-playing servers and unique gameplay experiences. While enhancing the game, FiveM can also impact network traffic and potentially interfere with other applications or devices on your network.
This comprehensive guide will walk you through the process of adding FiveM to your network filter, ensuring smooth gameplay while maintaining network stability and security.
Before delving into the specifics of FiveM, let’s understand the role of network filters.
Network filters, often implemented through firewalls, act as gatekeepers for network traffic. They control which incoming and outgoing connections are allowed or blocked based on predefined rules. These rules can be based on various criteria, including:
IP addresses: Specify source and destination IP addresses.
By configuring your network filter correctly, you can:
Improve network performance: By prioritizing or blocking specific traffic, you can optimize network resources for critical applications.
To effectively add FiveM to your network filter, you need to understand the characteristics of its network traffic:
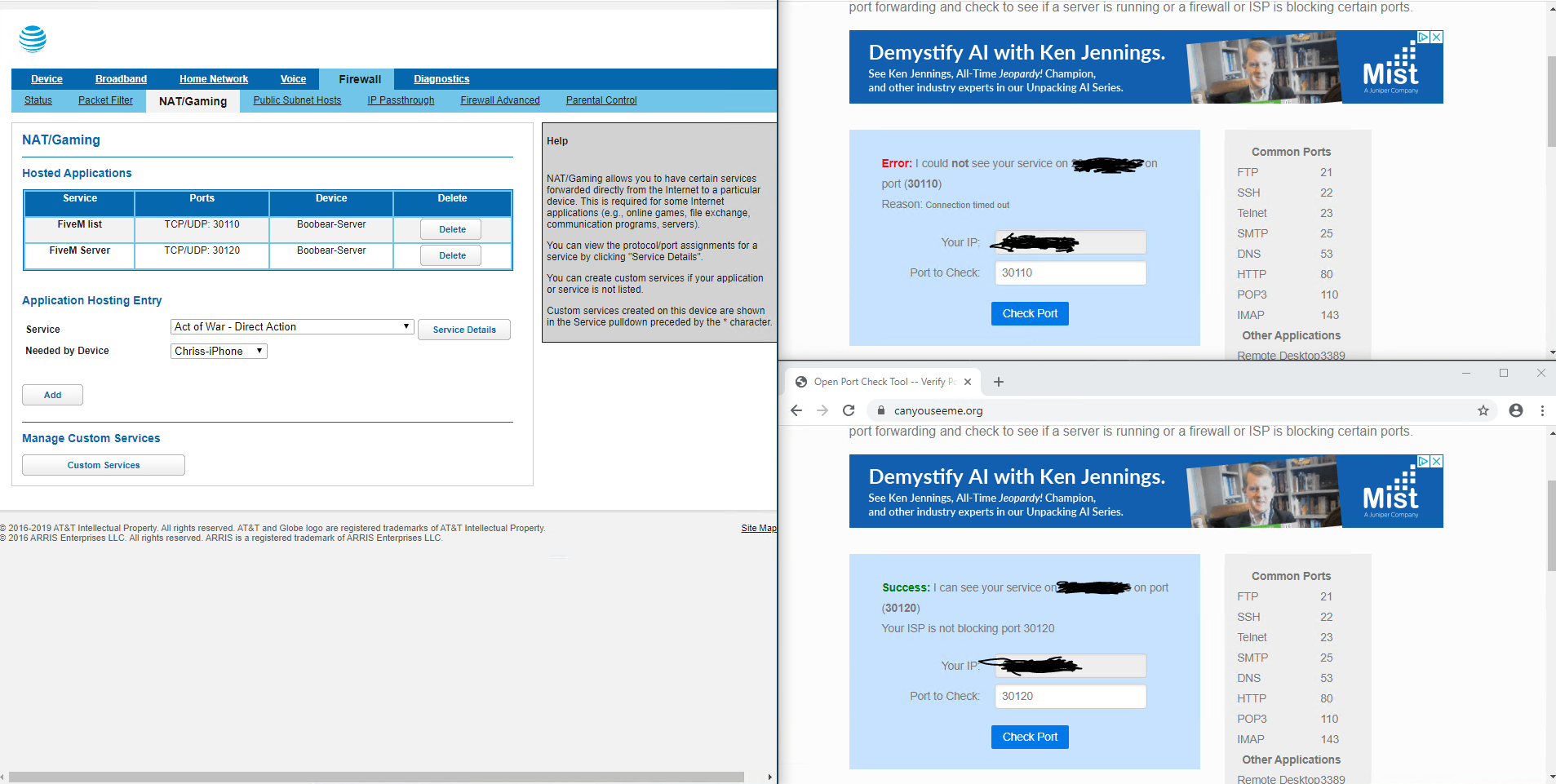
Default Port: FiveM primarily uses TCP port 30120 for communication.

The specific steps for adding FiveM to your network filter will vary depending on the type of firewall or network filtering software you are using. However, the general process involves creating a new rule or policy that allows or blocks traffic matching the characteristics of FiveM.
1. Access your firewall or network filtering software: This could be a hardware firewall device, software installed on your router, or a software firewall on your computer.
2. Create a new rule or policy: Look for options to create new rules or policies to control network traffic.
3. Specify the criteria:
4. Define the action:
5. Apply the rule: Save the rule or policy and apply it to your network.
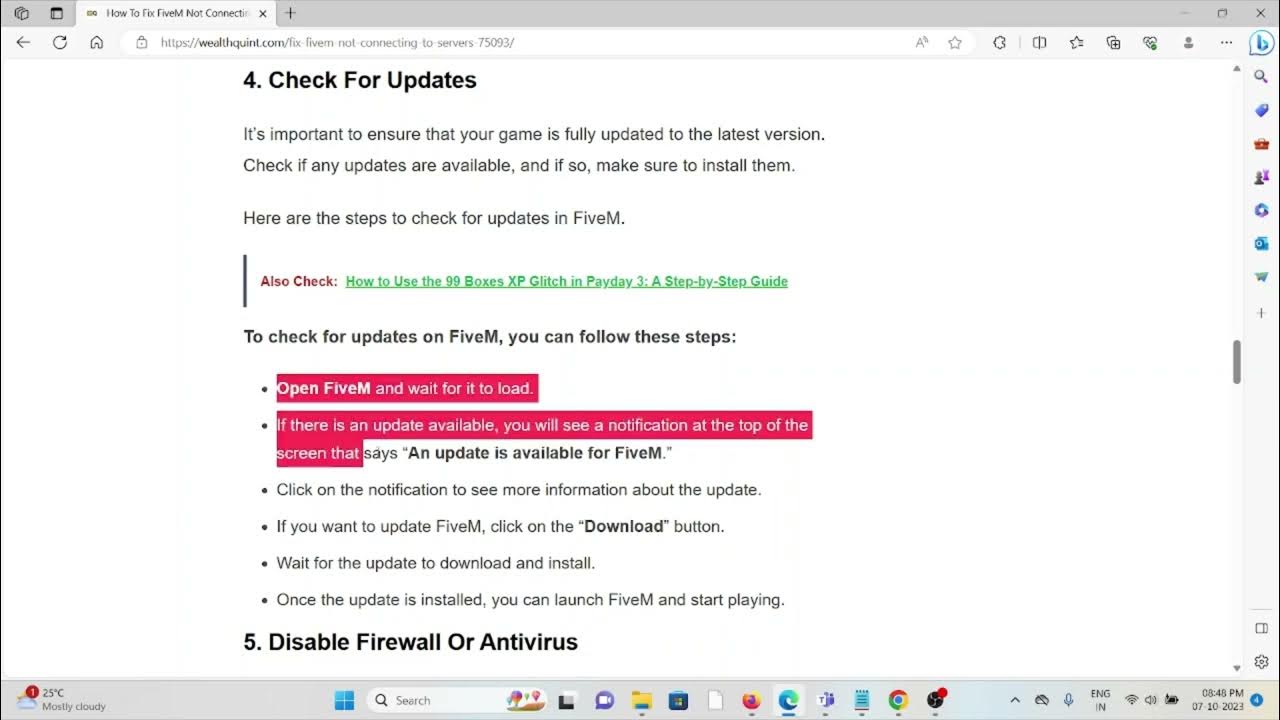
1. Open Windows Defender Firewall: Search for “Windows Defender Firewall” in the Start menu and open it.
2. Click “Advanced settings”: This will open the Windows Defender Firewall with Advanced Security window.
3. Create a new rule:
Test your configuration: After adding FiveM to your network filter, test your connection to FiveM servers to ensure it works as expected.
Application-level filtering: Some advanced firewalls and network filtering solutions allow you to filter traffic based on the application itself, rather than just ports. This can provide more granular control over FiveM traffic.
By carefully configuring your network filter, you can effectively manage FiveM traffic, ensuring smooth gameplay while maintaining network stability and security. This guide provides a starting point for adding FiveM to your network filter. Remember to adapt the specific steps based on your network environment and the type of firewall or network filtering software you are using.
By following these guidelines and exercising caution, you can enjoy the benefits of FiveM while maintaining a secure and well-managed network.
